To get secure access to internal networks, one usually employs one of the many variants of a VPN. When connecting from a normal computer, you can install basically whatever variant you wish. When using devices such as smartphones however, the number of supported VPN technologies is usually limited. Especially on non-open platforms such as the iDevices by Apple, you can not add VPN software yourself, contrary to the Android platform.
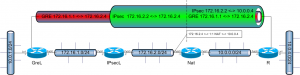
In this post, I’ll explain how to set up an IPsec (without L2TP) tunnel endpoint on an Ubuntu server, capable of handling an iPhone/iPad/iPod/iWhatever. The users will be authenticated against an LDAP directory.